What's The Good Keylogger For Mac
Revealer Keylogger Free is a competent if unremarkable keylogger for Windows. It can run at startup, hide itself from users, and protect access with a password. But basic features such as screenshots and email notifications aren’t available in the free version, and the program doesn’t log IP addresses. A good keylogger should be stealthy and not compromise the victim’s system by causing slowdowns, unexpected crashes, etc. It must use a strong encryption, too, otherwise antivirus software can pick up on it. Top 10 Best Free Keylogger for Mac Why keylogging is possible? Keylogging – that is making a record of the keyboard inputs made on a device – has been around for a long time.
Track web sites stopped at Receive a full checklist of all internet sites visited. Even if browser history is usually removed, our keystroke Iogger + recorder will collect it. Apple company's Safari, Google Chromium and Firefox are usually supported. Report talk and email Wanting to know who your loved one is speaking with?
Our hidden keylogger will maintain a report of all conversation. Top notch Keylogger for Mac also privately reports IM talks (Skype, Viber, Adium, iChat/Text messages), both edges.
Get reports via email Once the keystroke logger + recorder is set up, you gained't want to access that Mac once again - all reviews are sent immediately by email. Protect your teens online Elite Keylogger is usually the perfect household keylogger for keeping your teens safe. Know precisely who they are talking to and what images they are revealing online. Also if you don't check out the hidden keylogger reviews regularly, it's good to know they are right now there in an crisis. The security password tracker function makes certain you aren't locked out if you require to access your teenager's information in a rush.
Completely undetectable Top notch Keylogger PRO is definitely one of the best keyloggers on the market when it comes to total invisibility. This ideal keylogger remains totally hidden and does not display up in the Programs folder or dock. It can just be released by typing a top secret term and then a security password. /highpoint-launches-the-industrys-fastest-usb-30-raid-hbas-for-mac.html. Free keylogger vs PRO The major difference between the free and PRO variations can be that the free of charge keylogger edition is not concealed. It nevertheless requires a security password to become seen, but users of the personal computer will see it in the dock as an energetic application.
This a perfect keylogger for circumstances when you would like customers to know they are usually being supervised. But if you wish an invisible keylogger, you will require to. Are usually keyloggers legal?
Yes, hidden keyloggers are usually legal, simply because long as you have the pc you are setting up it on, or have got been given administrative benefits to the computer by the owner. Top notch Keylogger installation requires that you understand the Mac's management password.
The best keyloggers enable undetectable or open surveillance, based on your needs. Therefore download our keylogger and give it a try today!
A keylogger can become possibly a item of software or a small hardware gadget that can be utilized to catch the keystrokes that are usually entered on the keyboard. The equipment structured keylogger can end up being easily recognized because the actual device demands to end up being linked in between the key pad and the USB/PS2 slot. Nevertheless, as for a software program keylogger, it can become operate while becoming completely unseen and not really get noticed by typical computer customers. They'll have got to fully depend on safety software such as or to inform them that a keylogger can be present on the system, or else they possess no idea that everything that they perform on the computer is getting supervised. There are many reputable uses for a keylogger like as checking your children, making sure that they especially when chatting and making close friends with strangers.
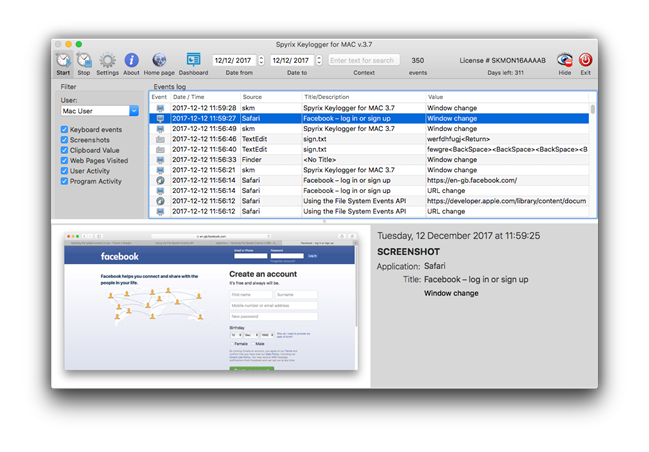
Or probably even checking your workers making certain that or leak out any confidential files. However it can also be used for unlawful purposes like as taking your buddy's password and etc. There are many software structured keyloggers discovered on the Web, some are usually freeware while others are usually shareware that need a paid permit to make use of. Generally talking, a shareware version of a keylogger normally has much better invisibility to prevent being discovered by sophisticated users, probably security software and also has more functions. As for the free of charge keyloggers, they are often extremely limited in functionality and stealthiness. After testing almost 2 dozen free of charge keyloggers, we've picked what we thought had been the greatest and categorized them into a top 10. Free of charge Keylogger It is capable to record keystrokes, clipboard data and web site addresses without the display catch which is fine for individuals who wear't wish to catch screenshots.
There are usually a few of invisibility settings such as the concealed setting hotkey (default Ctrl+Change+Alt+U), getting rid of cutting corners from begin menus and uninstall checklist. Ironically the most downloaded keylogging device from CNET download.com hardly produced it to this best 10 listing because the most essential stealth feature which can be beginning the program in concealed mode is certainly disabled in the free of charge version. You can fixed it to immediately start the program with Windows but it will display a tray symbol at notification area and anyone can access to it because there is definitely no security password protection feature. You can however manually conceal it by pressing the “Apply Spy” button to maintain it operating as hidden until the following reboot. REFOG Free of charge Keylogger REFOG is definitely a really popular company that offers a variety of keyloggers providing for house, company and corporate and business use but sadly the free of charge version is certainly very simple as most of the important features possess been impaired. The free of charge version of REFOG keylogger can only monitor keystrokes, stopped at sites, clipboard, ran applications and pc routines.
The biggest disadvantage would become the inability to run totally hidden because it shows a noticeable tray image in the notification area and thankfully the plan can at least become password shielded. We furthermore found out how to, which becomes out to become quite simple. DanuSoft Free Keylogger DanuSoft is definitely a basic and easy to make use of free device to capture keystrokes. The just way to conceal and unhide the program is by keying in a selected keyword, for instance the default hide keylogger keyword can be “HIDEKEY” while to show is certainly “SHOWKEY”. You cán configure DanuSoft tó immediately operate as stealth during system startup from the Beginning settings tab.
It doesn't possess the capability to shield the system by establishing a security password, although it runs as unseen in Home windows but not in job supervisor or explorer. This writer of this keylogger seems to have got abandon this project because it can be not discovered on the standard DanuSoft't website but can nevertheless end up being downloaded from CNET. True Free Keylogger After installing Real Free of charge Keylogger to log the keystrokes, operating it the 1st period will fast you to set a password to safeguard the system therefore that just you can access the configurations and see the wood logs. You can set a hotkey (defauIt Ctrl+Alt+A) to launch the program when it is certainly operating in stealth mode. It arrives with a scheduler to instantly start working and the log data files can become exported as a HTML file. The system folder is usually set as program feature and is usually only visible when the Cover protected operating system data files is uncontrolled in Folder Choices.
Revealer Keylogger Free Revealer Keylogger Free is usually the second nearly all downloaded supervising device in CNET DownIoad.com. After screening, we found that it will be very reactive and light on program usage. It can record keystroke, has multiple language support, startup configurations, capability to run with raised liberties, hotkey assistance (default Ctrl+Alt+F9) and automatic log cleanup. Screenshot capture, automated delivery options and extra stealth features are handicapped. The system can become protected with a security password, and is usually hidden in the táskbar and in ádd/get rid of programs. To uninstall, you can perform it by running the program, click on the issue mark icon at the best right, go to Program end and select Uninstall.
Pay out attention during the installation because it prompts to install adware. May you can use this program code for each essential. And operate while your personal computer is definitely on. $(captureInput).keydown(functionality(event) //Press startDOWNPress = (new Time).getTime;.
//Codigo no util para el ejemplo. $(captureInput).keypress(function(event) //KeepPress startPressUP = (brand-new Date).getTime;.//illustration program code. $(captureInput).keyup(functionality(event) //Discharge startUPDOWN= (fresh Date).getTime; But to perform that properly, you would need an particular gadget. It can be very hard to measure the period you are usually pushing a key simply by software, because this information is usually no related for key pad function, just to replicate a key, therefore the period measured is much longer than 1 milisecond. However you can install an digital signal capturer between your key pad and your personal computer in order to obtain all digital indicators and sending time.
I have got an worker who consistently does not pay attention to me wondering her to not really run conversation or live stream videos on her personal computer. She is definitely now on our pc that has our financials ón there; and l caught her again with live life loading on when I went in. Im heading to move over our worker handbook once again, make her SIGN EACH paragraph and after that put this on here. We're also a little non-profit, and to eliminate our financials would be the finish of us. Yes, I perform backup; but still - there'beds no need for her to carry on this. (I have got to possess solid proof of her continual lack of executing duties in purchase to provide this before my panel for dismissal. Sad fact.) Do these keyloggers display when the personal computer is transformed on and when it will go dormant for a even though (20 minutes?) it displays computer shut?
She comes in late when she understands im out there and after that fibs about it.) sigh.
Why keylogging will be possible? Keylogging - that is making a record of the keyboard inputs made on a gadget - has ended up around for a long period. Since the days of mechanised typewriters in truth! Presently, we are very usually talking about a software situation, the recording of exercise - keystrokes, and significantly, much even more - on a cellular cell phone. Whatever the means of insight, of inquiring your telephone to do something, that demands a order, a message, a transmission to become sent to the operating system. Whether it become iOS, Windows, Mac Operating-system or Android, that order can become intercepted and documented for later inspection. That is definitely keylogging in a nutshell. Apple is famous for its consumer safety.
But we can come good Macintosh keyloggers items to help us therefore;ve some complications. Why keylogging should be utilized?
In all situations, if you have got the authorization of the consumer of the focus on phone, the phone whose activity you would like to report, then there can be not really any problem. With your kids, that should be straightforward.
The data, including deleted items, is synced just minutes after the activity as opposed to iCloud backups being daily at best. Telecharger elcomsoft phone password breaker. Call logs, browsing history and Safari open tabs, notes, calendars and contacts are synced in nearly real time with little or no delay. Elcomsoft Phone Breaker extracts synced information in addition to iCloud backups. By obtaining FileVault 2 recovery keys from the users Apple account, Elcomsoft Phone Breaker can instantly unlock and mount encrypted FileVault 2 volumes. Elcomsoft Phone Breaker is the first GPU-accelerated tool to recover plain-text iOS backup passwords, and remains the only tool to decrypt the keychain.
With employees of a business, provided it is definitely a firm funded telephone, and the monitoring is only of company routines, that should not really be a problem possibly. We can imagine a conversation, though it might not end up being an simple one, where your partner in life might furthermore give authorization for their phone to end up being monitored. It can be likely that you would think about making use of a keylogger in a circumstance where there is certainly some problem between the events, possibly put your trust in is not 100%.
It is definitely likely that a keylogger is certainly a much less expensive remedy than any alternative. However, our guidance can just end up being that you continue at your own cognizance. We possess some greatest keylogger for Macintosh for you below.
Best 10 Best Keyloggers for Mac pc. PROS: Provides the helpful capability to block specific sites. Generally clear and helpful guidelines and assist.
Center to higher range price Downsides: Full functionality demands the iPhone to end up being jailbroken. Some of the Quick Messaging apps are usually not really logged. Advantages: Has password defense against unauthorised recognition or make use of. Completely undetectable report of all keystrokes. Fine looking interface.
Downsides: Mixed, really good or extremely negative, reviews of client experience. Just details the activity in Instant Messaging apps from one aspect.
Advantages: It takes a picture of anyone making use of the cell phone - you could make use of it for the safety of your personal phone! There is certainly a test version after that pricing is definitely competitive. CONS: The free of charge version is usually only a restricted trial. Require physical entry of the focus on mobile phone. No iOS version. PROS: Presents the reported activity in reasonable groups. Intercepts and pads listed internet addresses.
Downsides: Available in English only. PROS: Records sound. Wood logs both edges of IM marketing communications.
Good reporting options. CONS: The set up can become quite complex. Stealth may end up being jeopardized in the free of charge version.
Advantages: Basic to make use of. Open source, under constant development, might become worth long term consideration.
CONS: Very basic with minimum choices. Can become recognized and uninstalled. Advantages: Will make a sign of all usernames and passwords - possibly very helpful information. Slick interface. CONS: Cannot block out websites. Installation seems a little Iong-winded.
Stealth setting is suspicious. PROS: It provides a extremely light footprint and provides really little fill to your pc. Records both sides of Instant Messaging chats. Negatives: This will be a limited version - full functionality is definitely only gained with the paid version. Appears that there is definitely a quite limited user base with really little responses.
No e-mail choices for reviews. Advantages: Gives you the chance to monitor live, the current action on the targeted device.
Live monitoring is more improved by becoming capable to take screenshots. Can block selected sites. CONS: Does not monitor email messages or accessories. Has restricted storage capacity for screenshots which have got been used. PROS: A solid listing of choices.
Password shielded. A scheduler fór recordings will help limit overload. Downsides: The restricted quantity of downloads and testimonials do not really promote full confidence. Best Keylogger for Andróid-Spyzie Everyone wiIl possess their personal reasons for using a keylogger. Your reason may well become an completely positive one. We are usually of the opinion that if you are heading to perform something, you may as well do it in a fully committed method. It will be a variant of tugging that plaster off simply because shortly and mainly because quickly as you can.
It is certainly a variation of if you would like anything performing well, you may as well do it yourself. It is definitely another method of stating in a lot of cliched methods if you are heading to perform something you should perform the greatest that you cán. In an expanded planet of technologies, it is very important to sustain handle over all your appliances. Portable devices like capsules and cell phones possess become a fundamental necessity of lifestyle. These devices consider our personal information, information about our daily job and everything we need to communicate with our friends and household. Among them the application Spyzie it is definitely the best option to control your cell phone. Explanation If the issue is already rising in your brain in moving an Android gadget or IOS, and after that make it apparent in the very first location.
Spyzie is definitely a web-based remedy. You can open a free of charge account and link to both the Android/iOS software and the web-based website if the device is already installed on your device. As soon as in procedure, Spyzie will bring out the function that can be designed to. You can maintain an eyesight on your contact records, text message messages, Gps navigation place of your phone, the history of your Web browser.
All the bookmarks are saved on your device, the pictures, the work schedule and the activities of all the programs that are being installed in the procedure or in the telephone. How to make use of Spyzie Keylogger to monitor Android gadget?. The first factor you require to perform is. For that, go to Spyzie.com and generate an account with email id and chosen password. As soon as done, download the ápp on your device. After the registration process will be complete, supply some comprehensive information about the device you want to track with Android keylogger. Before you can set up the app, you will require to understand a little bit about installing an unauthorized ápp.
You will need to move to the Creator Option on your device to allow the installation of an app that is not really from an authorized source. Once performed, you will become able to install the app effortlessly. Now go the site of Spyzie and download the Series account crack that you will need to set up on the mobile gadget you want to monitor. After the set up is full, open up the Spyzie ápp on your gadget and log in with the credentials that you produced earlier. To use Google android keylogger you will need to permit the permission it will request for. Once performed, you will have got to stimulate your supervising on the device.
Right now, you can remove the app on the focus on gadget and leave it as it will be. The app will keep operating in the background and spy on Android device. Now you can come back to your own device and sign in with the same credentials and go to your dashboard.
As soon as in the, you will be capable to spy all the cultural Apps but just those accounts that will end up being utilized on the targeted portable. Right now, you will become capable to spy on any public App account, the text messages, photos and videos it stocks. Generally, you will able to monitor it 24 Back button 7 from your dashboard.